The frequent cases of healthcare data breaches have raised concerns among all healthcare actors. For patients, health data leaks may lead to the exposure of personal information. For providers and payers, data breaches may result in severe penalties for neglecting the value of data privacy in healthcare. That’s why today we are discussing the difference between RBAC and ABAC and their benefits in healthcare.
In the article about the importance of data security solutions in healthcare, we shared HIPAA’s statistics that reported healthcare data breaches doubled in five years. For that reason, national agencies put their efforts into designing solutions for advancing the security of patient information and ensuring effective health data access control for preventing leaks of sensitive information. This includes exploring ABAC solutions and comparing access control models to find the most effective approach.
Today, we will discuss the most popular security models for accessing healthcare data, focusing on RBAC and ABAC policies and how they can be transitioned from RBAC to ABAC for enhanced security.
Role-Based Access Control
What is RBAC?
RBAC (Role-Based Access Control) is a security model that limits access to healthcare data based on the role of a client (e.g., physician, patient, application). Hence, the RBAC approach refers to granting access to a client based on their role.
Why do healthcare systems need RBAC?
Sensitive patient data must remain confidential. Unauthorized access to such information can lead to privacy breaches or medical identity theft. Therefore, it is essential to have a robust security system, such as RBAC, to ensure that only authorized users have access to sensitive data. Role-based access control in healthcare is crucial for maintaining data integrity and compliance with regulations.
RBAC Roles and Permissions
RBAC assigns roles to users based on their job functions or titles, such as assigning different sets of permissions to a doctor compared to a nurse or receptionist. Moreover, RBAC gives permissions to roles rather than users. Therefore, the role assigned to users determines their permissions. For example, if a nurse is assigned the “Nurse” role, they will inherit the permissions set to that role. These permissions can define the permitted actions, such as access to read, search, update, create, or delete. Understanding these distinctions is crucial for achieving ISiK Compliance, as it ensures that access controls align with standardized data exchange protocols in healthcare systems.
Benefits of RBAC
- Improved security: RBAC manages access to sensitive data by restricting it only to authorized personnel, ensuring the confidentiality and security of patient information.
- Simplified user management: RBAC assigns permissions to roles instead of individual users. As a result, adding or removing user permissions becomes easier.
- Security regulations compliance: RBAC maintains compliance with data privacy laws such as HIPAA by ensuring only authorized personnel can access sensitive data.
- Higher productivity: the productivity of systems with RBAC is higher than with individual verification of access levels for each user or with ABAC systems.
Attribute-Based Access Control
What is ABAC?
In RBAC, we define access control policies based on roles that grant permissions to a user. In contrast, ABAC policies rely on attributes that describe the user, the accessed resource, and the request context. These attributes may include the user’s identity, location, device type, or any other relevant information that enables a system to make access control decisions. The ABAC security model offers a flexible and dynamic approach to managing access control.
Why do healthcare systems need ABAC?
ABAC is often compared to the traditional security model RBAC. ABAC enables access decisions based on the attributes linked with the subject, object, and environment. When comparing RBAC and ABAC, it’s important to remember that the effectiveness of each approach depends on the context and requirements of the task. The difference between role-based and attribute-based access control lies in their approach to managing permissions and access.
RBAC provides access based on the client’s role, making it better suited for cases where access needs to be granted to a client with no attributes. ABAC offers higher granularity and flexibility, but this approach requires more attention during implementation.
The role of attributes in expressing access control policies
ABAC uses a policy engine to evaluate access requests and decide whether to grant or deny access based on the associated attributes. The policy engine considers multiple attributes and assigns different weights depending on the sensitivity of the resource being accessed.
Benefits of ABAC
- Higher granularity: ABAC provides a more detailed control level by granting or denying the right to access healthcare data based on specific attributes.
- Dynamic policies: ABAC considers a broader range of factors than RBAC, which allows for implementing data access control policies that adapt to changing circumstances and attributes (e.g., time of day, location, or device type).
- Data-centric security: ABAC defines access control policies according to the sensitivity of the accessed data. This approach grants or denies access based on attributes of the data such as its classification level, type, or owner.
Understanding the differences and benefits of attribute-based access control vs. role-based access control can help healthcare stakeholders implement the appropriate access control policies based on their specific needs and requirements. The SMART on FHIR framework supports the use of both RBAC and ABAC to provide a more flexible and granular approach to access control, which allows for zooming in on the features of both methods.
RBAC In The SMART on FHIR Framework
The SMART on FHIR framework supports RBAC, which declares the range of functionality requested by a client application by the Authorization Server, also known as scopes. The three levels are patient, user, and system.
- The patient is the zeroth level of access, which means the patient and the application accessing the FHIR server are only permitted to access data related to a specific patient.
- The user level is typically assigned to a doctor or other healthcare professional who accesses the FHIR server through an application. The server only provides access to the resources the user is allowed to access.
- The system level is used for applications that access the FHIR server without human interaction. This level specifies which resources can be accessed by the application.
In FHIR servers, any resource can work as an access object. The role is specified by writing the following:
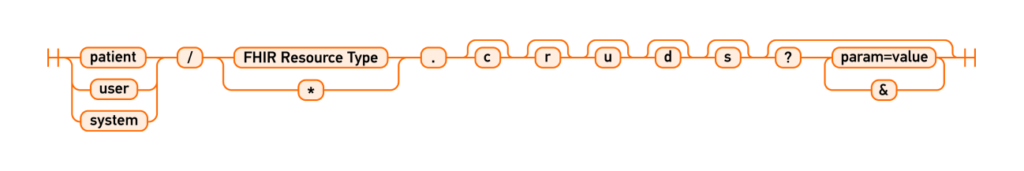
For example, “patient/Location.read” is an RBAC-based access request where “patient” is the role. Similarly, “system/Patient.read” is another role-based access request.
In SMART on FHIR 1.0.0, three types of actions can be performed on FHIR resources: read, write, and *. In SMART on FHIR 1.0.1 and later versions, scopes specify more detailed access controls, including “r” for read, “s” for search, “d” for delete, “c” for create, and “u” for update.
The role/scope for SMART on FHIR 1.0.1 and later versions can be specified as follows: “patient/Observation.rs” or “patient/Observation.crs.“
The ONC-compliant Kodjin FHIR Server supports SMART on FHIR 1.0.0, which supports read, write, and “*” wildcard-based actions for FHIR resources. The RBAC approach is used to improve the security of patient data when accessing EHRs, highlighting the importance of robust FHIR security measures for protecting sensitive information.
ABAC In The SMART on FHIR Framework
The primary purpose of an FHIR server is to serve a client. In an FHIR server, the client is another program launched by a physical user (e.g., healthcare professional or patient) who will not access the FHIR server for information on their own. This application either has a front end of the FHIR server or accesses another FHIR server. Thus, the SMART on FHIR framework always refers to the interaction between two applications: the client and the FHIR server.
SMART on FHIR is a hybrid model that can include both RBAC and ABAC. With the addition of the “launch/patient” or “launch/…” scope, users are allowed to work with resources at the patient level of access, but they must have the patient’s context. Hence, the “launch” scope transforms RBAC, which includes read, write, wildcard, and CRUDS scopes, into ABAC.
The SMART on FHIR specification defines that the context can be anything, such as launch/encounter, launch/location, or other contexts. In SMART on FHIR, everything depends on the attributes used in the launch-context.
According to the SMART on FHIR specification, the “launch” is not mandatory for user and system scopes, so authorization occurs under RBAC role-based authorization (there is a role and definition of operations allowed for this role to perform on an FHIR resource).
Main Differences Between RBAC and ABAC
RBAC, or Role-Based Access Control, operates based on predefined roles and permissions. It simplifies access management by assigning permissions to roles rather than individual users. This approach ensures authorized personnel, such as doctors, nurses, or receptionists, can access sensitive data while enhancing security and compliance. RBAC excels in scenarios where access control needs align with predefined roles and straightforward user management.
On the other hand, ABAC, or Attribute-Based Access Control, takes a more dynamic and granular approach to access control. It considers many attributes associated with the user, accessed resource, and context to make access decisions. This flexibility allows organizations to implement context-aware policies that adapt to changing circumstances and requirements. ABAC thrives in complex access scenarios where fine-grained control based on various attributes, such as user identity, location, and context, is essential. The difference between ABAC and RBAC is crucial for understanding which model to implement based on specific needs.
The specific environment, access control needs, and regulatory compliance requirements of a project should drive the choice between RBAC and ABAC.
RBAC vs. ABAC: Which One to Choose
When comparing RBAC (Role-Based Access Control) and ABAC (Attribute-Based Access Control) to determine which to choose, it’s crucial to evaluate the advantages and limitations of both models.
Access control is essential for safeguarding organizations against data breaches. However, we recommend going for the expertise of industry professionals to consider specific environments and requirements to make an informed decision about which model aligns better with your project’s needs. Understanding RBAC or ABAC is essential for making the right choice in access control models.
THE KODJIN TEAM IS READY TO SOLVE THE MAIN PROBLEM OF THE ABAC APPROACH
The SMART on FHIR specification explains where a system that accesses the FHIR server can obtain all roles except for the launch/patient scope. However, this may become a significant obstacle to achieving regulatory compliance in healthcare and implementing SMART on FHIR for more secure healthcare data access.
Using the SMART on FHIR framework for facilitating interoperability in healthcare ensures sensitive healthcare data is only accessed and exchanged by authorized individuals/applications.
Our certified FHIR specialists can solve this problem and develop the most efficient solution according to your project budget. Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) are two security models used to control access to resources via robust authentication and authorization mechanisms.
FAQ
- Which model RBAC vs ABAC is better suited for complex access scenarios?
RBAC (Role-Based Access Control) is better suited for more straightforward access scenarios where access can be effectively managed based on roles. It assigns permissions to roles (e.g., doctor, nurse, receptionist) and simplifies user management by granting permissions to these roles. In contrast, ABAC (Attribute-Based Access Control) is more flexible and suitable for complex access scenarios requiring detailed control based on attributes like user identity, location, and context.
- Which model ABAC or RBAC is more flexible for access control?
Both ABAC (Attribute-Based Access Control) and RBAC (Role-Based Access Control) offer flexibility for access control. Still, their suitability depends on the specific context and complexity of the access control requirements.








